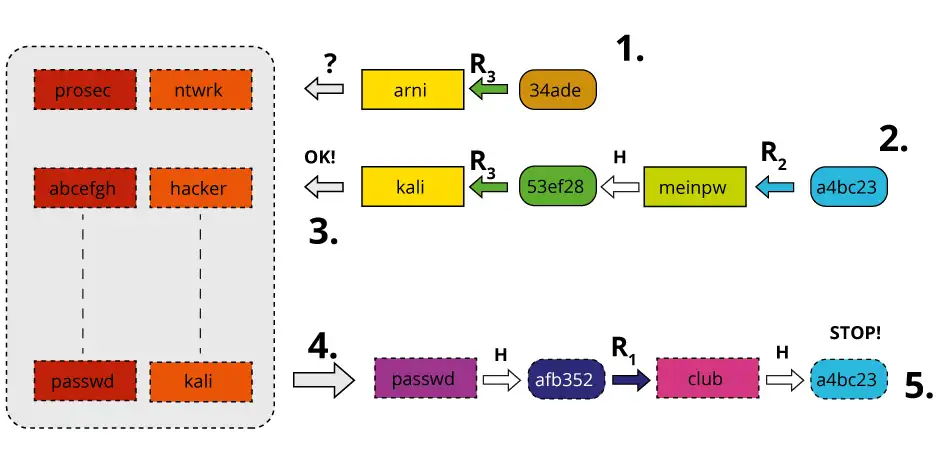
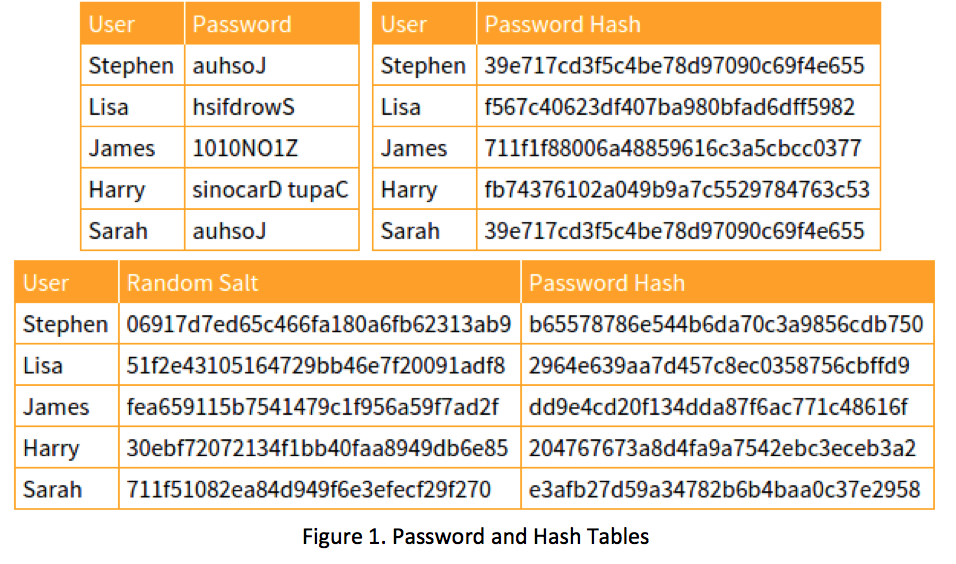
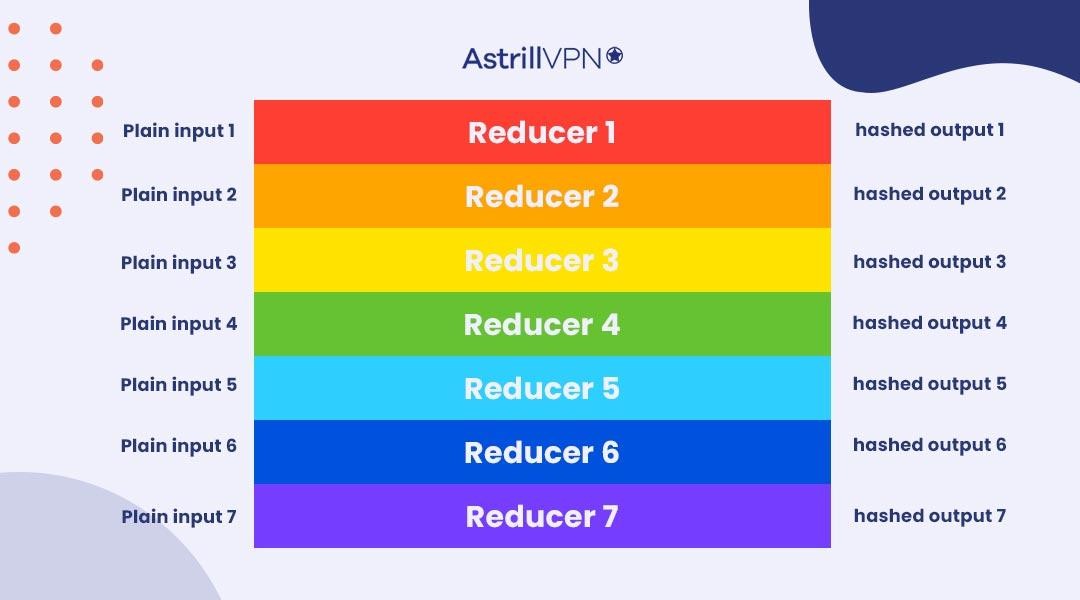
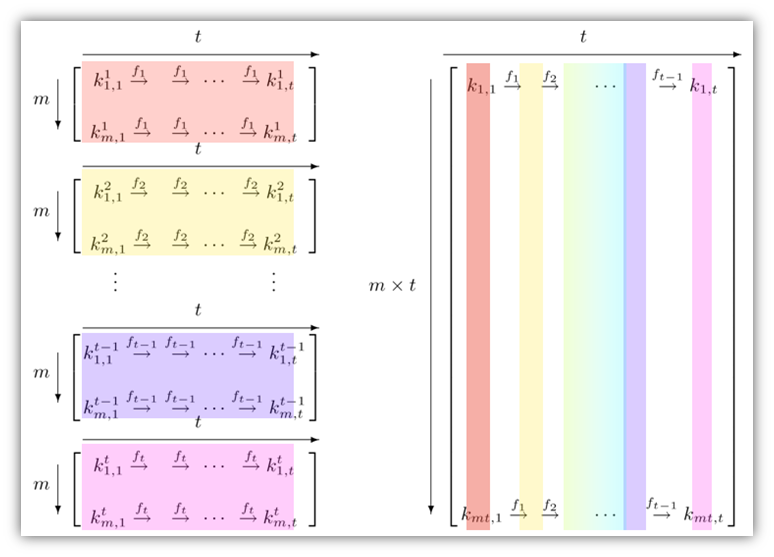
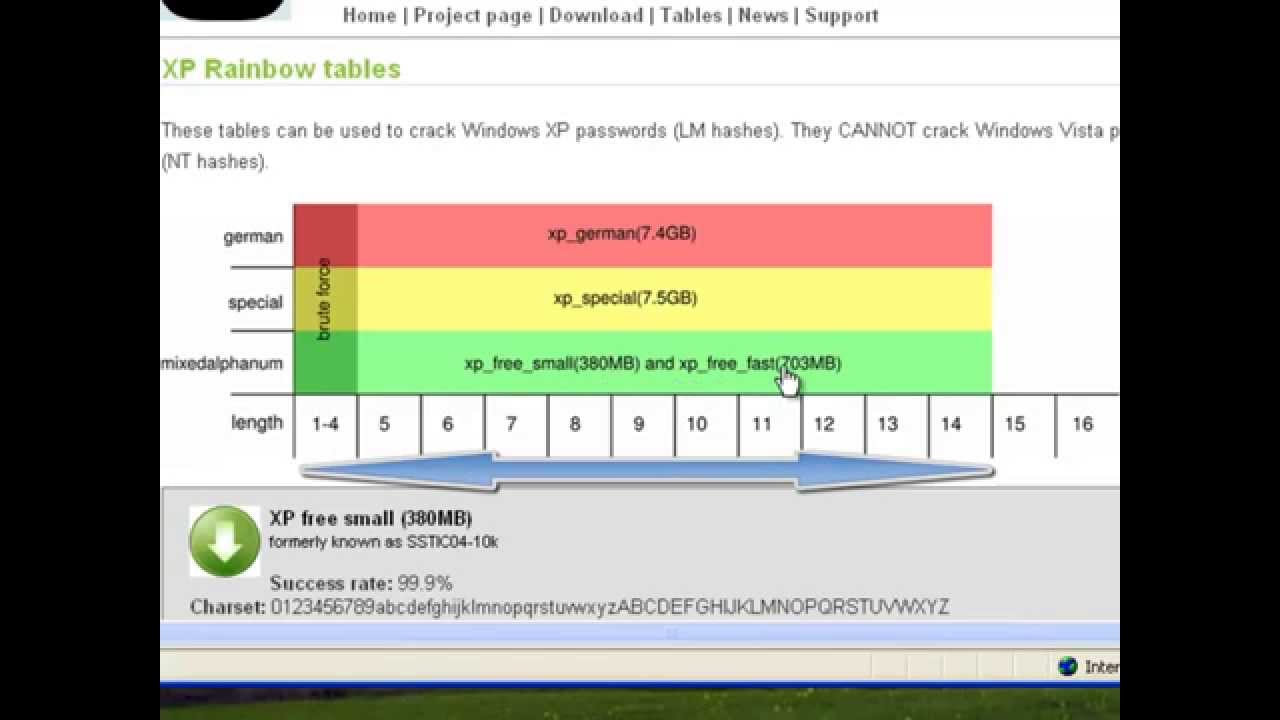
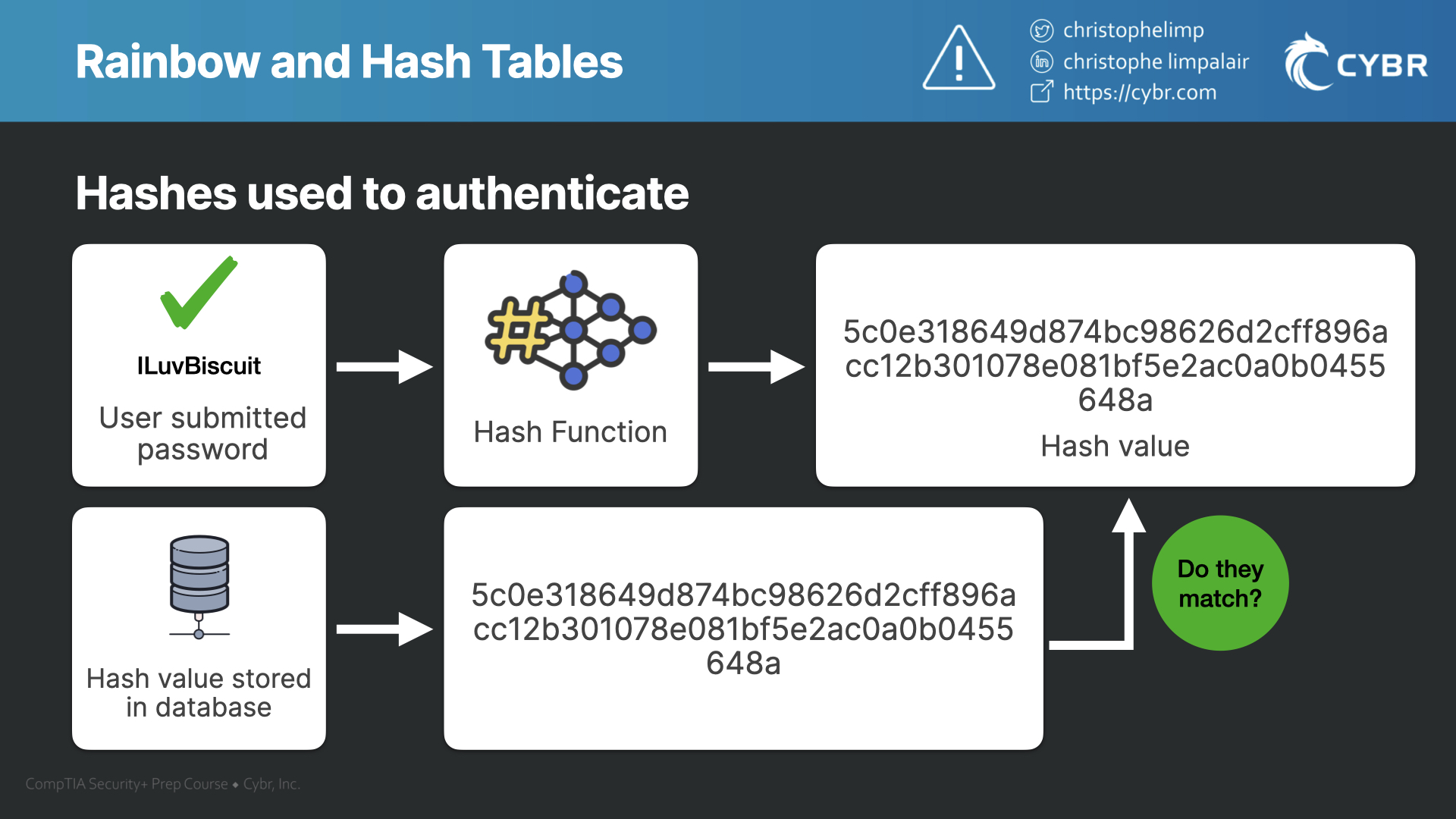
International College For Security Studies - ICSS - A rainbow table attack is a type of hacking wherein the perpetrator tries to use a rainbow hash table to crack the passwords stored

Amazon.com: Nepnuser Rainbow Table Runner Rustic June Pride Month LGBTQ+ Party Decoration Linen Farmhouse Home Dining Room Kitchen Table Decor (13" x 72") : Home & Kitchen

Whiz Security - Rainbow Table Attack A rainbow table attack is a type of hacking in which the attackers tries to use a rainbow hash table to crack the passwords stored in